The most common DFIR incidents

[ad_1]

Digital forensics is increasing although getting much more tied with incident reaction, in accordance to the most recent Condition of Business Electronic Forensics and Incident Response study from Magnet Forensics. On the other hand, some electronic forensics industry experts are burned out and have to have extra automation and leadership in the DFIR industry, wherever selecting is tough.
This study from Magnet Forensics, which develops digital investigation remedies, was conducted involving Oct and November 2022.
Leap to:
Electronic forensics ever more included with incident reaction
Electronic forensics, in some cases named computer forensics, has been an experience area that was typically deployed on one computer systems for numerous yrs. The common use conditions have been to obtain info on an employee’s pc who was suspected of committing an offense, or investigating legal or malware troubles such as details stealers.
Around time, attacks have developed in complexity and dimension and target quite a few computer systems or servers from corporations, normally at the similar time. Electronic forensics, which was all about analyzing total really hard push copies in an offline mode, observed a twist when it became vital to evaluate working devices.
As a final result, electronic forensics discovered new methods to integrate that complexity with incident response teams. It allowed a lot more deep-dive evaluation on programs when not shutting them down, and now digital forensics and incident reaction are generally alongside one another in the SecOps crew in just the Protection Operations Middle.
Specific attacks are ordinarily the case in which digital forensics will work preferably with incident reaction. Though incident reaction operates on containing, resolving and recovering from an incident, electronic forensics may be the finest answer to come across the root lead to of an incident.
The learnings from each incident response and electronic forensics actions assistance businesses obtain the weak places in their defenses and put into action new safeguards and processes.
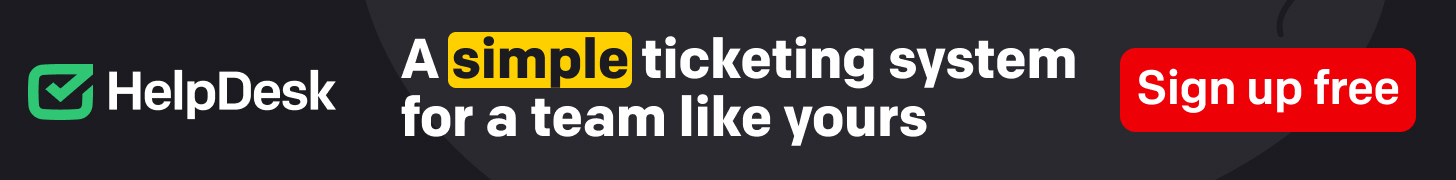
Most prevalent DFIR incidents
According to Magnet Forensics, information exfiltration or IP theft represents 35% of the in general exercise and is the most widespread DFIR incident, followed closely by organization electronic mail compromise (Figure A). Fourteen per cent of the survey respondents indicated that their business encounters BEC frauds incredibly regularly. Other frequent incidents are personnel misconduct, misuse of belongings or coverage violations, internal fraud and ransomware-contaminated endpoints.
Determine A
Knowledge exfiltration, IP theft and ransomware have a enormous influence on businesses. DFIR experts have a tough time operating on it, because experience and equipment are important to swiftly look into ransomware and facts breach incidents, even though cybercriminals test to render these investigations as tough as achievable.
The troubles of evolving cyberattack methods
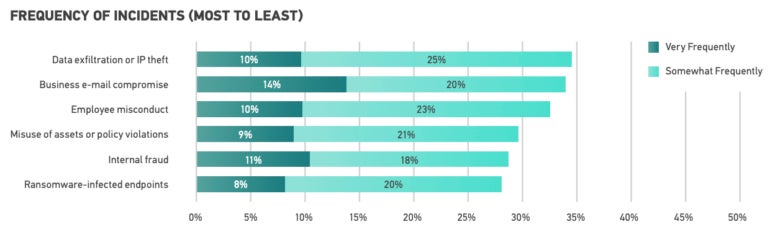
Attacks are evolving in measurement and complexity, with danger actors employing a lot more tactics to make detection more challenging as a result, 42% of DFIR industry experts reveal evolving cyberattack tactics present either an severe or significant issue in their business.
Keeping up to day about these cyberattacks is a problem, with businesses relying more on R&D experts focusing on equipping the business with new and ever-evolving tactics, approaches and techniques. Excellent resources of information about evolving threats consist of MITRE, CISA, and LinkedIn or Twitter accounts of cybersecurity researchers.
Much more automation for DFIR is wanted
A great deal of repetitive duties need to be completed in DFIR, and resources automating individuals duties are often needed.
SOCs presently make use of automation as significantly as feasible, as they will need to offer with telemetry, but automation for digital forensics is different, as it typically wants knowledge processing by orchestrating, performing and checking forensic workflows.
Fifty percent of DFIR pros point out that investments in automation would be significantly important for a array of DFIR features, as workflows still rely far too considerably on the guide execution of quite a few repetitive jobs.
Additional than 20% of the survey respondents indicated automation would be largely beneficial for the distant acquisition of target endpoints, the triage of goal endpoints, and processing of electronic proof, as perfectly as documenting, summarizing and reporting on incidents.
The survey respondents indicated that the increasing quantity of investigations and data is either an extreme (13%) or big (32%) challenge (Figure B).
Determine B
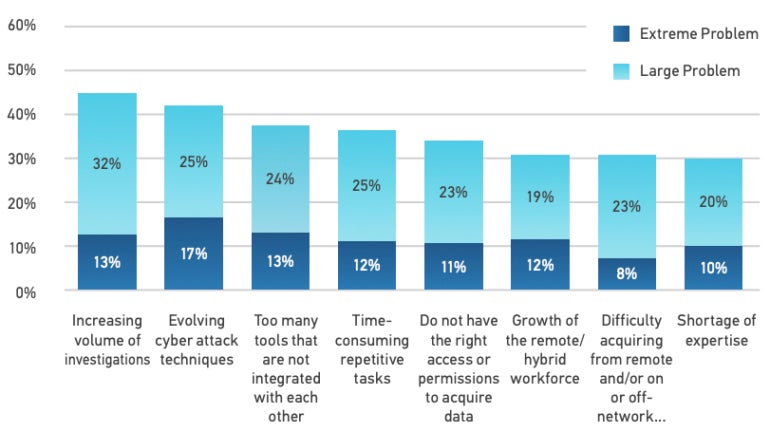
DFIR staff worries
Virtually 30% of corporate DFIR practitioners agree that investigation tiredness is a serious challenge, when 21% strongly agree that they truly feel burnt out in their jobs. The volume of investigations and facts, and the worry brought about by the necessity of jogging incident responses rapidly, tends to make it hard for people gurus to relax. Automation could assist help save these experts time and empower more rapidly assessment.
Recruitment is indicated as a major obstacle by 30% of the study respondents, although onboarding new DFIR experts can also be complicated simply because the job might range a great deal based on the enterprise for occasion, this could effect the applications utilised (Determine C).
Figure C
Extra DFIR leadership is necessary to support with facts and rules
A field under this kind of immediate evolution demands educated and decisive management to established strategies and direct sources in an successful way. Leaders impact the way DFIR pros can proficiently entry data sources they need, which is often tough, as far more than a 3rd of the survey respondents indicated.
The greatest contributions to wasted assets are the absence of a cohesive incident response system and strategy and the lack of standardized procedures (Figure D).
Determine D
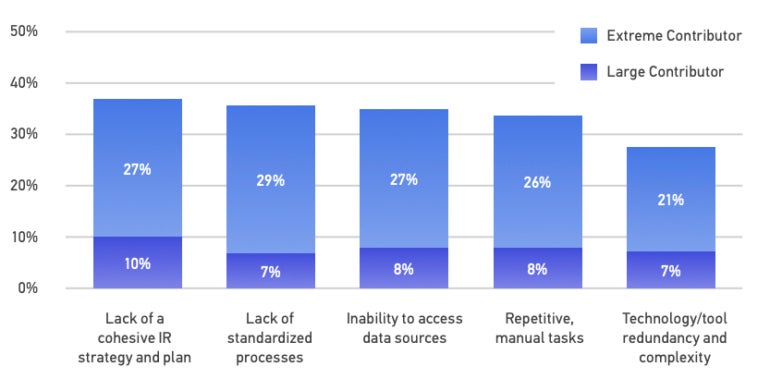
Rules are another challenge for DFIR pros. For occasion, 67% of DFIR pros indicated that their role has been impacted by new reporting laws, and 46% of the respondents claimed not possessing plenty of time to thoroughly recognize new and switching laws. Leaders need to recognize laws and determine how to deal with them, maybe by releasing up DFIR teams’ time to analyze the rules or consulting with the company’s lawful office.
Outsourcing with DFIR investigations is widespread
Most corporations typically outsource elements of their DFIR investigations, mostly due to the fact there is a absence of these expertise internally. Almost 50 percent of the respondents (47%) show the absence of expertise as the prior explanation for making use of assistance suppliers, whilst the 2nd purpose (38%) cited is not owning the expected toolset, which might be very highly-priced in some cases.
DFIR recommendations for enterprises
Providers should spend in DFIR solutions that prioritize velocity, precision and completeness. More delays signifies much more risk when it comes to analyzing incidents.
Automation really should be strongly enforced to assist DFIR specialists minimize burnout and minimize investigation delays.
An incident response system is essential. The plan will explain roles and obligations and element how forensics and incident response desires to be finished. It should really also assist accessing data with crystal clear directives and indications as to who presents what in the firm. Important positions to deliver accessibility to facts should be reachable 24/7.
Rules and legislations will need to be totally recognized by DFIR groups. Much more commonly, every little thing that could be carried out in advance to put together for potential incidents should be thoroughly thought of and performed when not performing on an incident.
Disclosure: I work for Development Micro, but the sights expressed in this short article are mine.
Browse upcoming: Safety Incident Response Policy (TechRepublic Premium)
[ad_2]
Source link Digital forensics and incident response (DFIR) is the scientific practice of investigating and responding to incidents in a digital environment. DFIR focuses on preserving evidence and understanding the source of an attack to ensure that it is not repeated. These investigations often involve identifying the sources of malicious activity and mitigating damages. As the digital world continues to evolve, DFIR is becoming an increasingly integral component of information security.
DFIR investigations may involve a variety of incident types, each with their distinct characteristics. Some of the most common include data breaches, malware outbreaks, and malicious insider activities.
Data breaches are one of the most common DFIR incidents, in which unauthorized parties gain access to sensitive information or data. This may include the exfiltration of data or other methods of data leakage. Incidents of this kind often involve malicious actors who attempt to monetize stolen data for personal gain.
Malware outbreaks are another type of incident that may be encountered. A malware outbreak is an event whereby malicious software is distributed and devices are infected in order to gain control or steal valuable data.
With regards to malicious insider activities, privileged users or contractors may attempt to gain unauthorized access to sensitive information. Such activities may be performed in order to steal data, impede the functioning of systems, or gain a financial advantage.
These are only some of the types of DFIR incidents that may be encountered, and it is likely that more will emerge as the digital world continues to evolve and attackers become more sophisticated. Therefore, it is essential that individuals and organizations maintain a comprehensive security strategy to ensure the safety of their data. Such measures may include training employees to use secure passwords, regularly patching software and systems, and utilizing two-factor authentication where possible.
Overall, DFIR is essential for ensuring the security of digital environments. By understanding the most common DFIR incidents and prevention measures, individuals and organizations can best protect their data and digital assets.