New cybersecurity BEC attack mimics vendors
[ad_1]
Economical source chain compromises, a subcategory of BECs, show up to be ascendant and hugely effective. Irregular Security has determined 1 pernicious danger actor that it has dubbed Firebrick Ostrich, which is working with a subtype of these gambits to trick targets into creating payments.
The organization beforehand discovered 4 forms of monetary provide chain compromise, which dispense with impersonation of inside executives at the concentrate on organization and rather have on the garb of one of the company’s vendors. Irregular Safety says Firebrick Ostrich has utilized a person of these varieties of fiscal provide chain compromises — 3rd-party reconnaissance attacks — to dedicate 346 BEC campaigns dating back again to April 2021, impersonating 151 companies and making use of 212 maliciously registered domains, just about all in the U.S.
Crane Hassold, director of menace intelligence at Abnormal Security, explained the sum of income that can be gotten from exterior, 3rd-get together impersonation is three instances larger than traditional BEC exploits, and that their accomplishment stems from awareness deficit, as businesses and their staff are experienced to search for email messages impersonating an inner executive, not a vendor.
“Also, when you glance at 3rd-party reconnaissance and other financial provide chain attacks, the performance of the lure is in the amount of facts they are equipped to set in email messages — details that tends to make them glimpse a large amount far more real looking than other sorts of BEC,” he reported.
SEE: Cell machine security plan (TechRepublic High quality)
Hassold famous that tens of billions of bucks have been shed due to BECs in any provided yr, and that BECs are a main bring about of financial reduction at enterprises going back again to 2016.
“BECs definitely exploded and peaked in the very first 6 months previous 12 months, driven by attackers impersonating exterior entities, a large adjust since, since its inception, BECs have mostly included impersonating internal entities,” he said. “BEC actors have discovered third parties — such as sellers — as a weak hyperlink in the chain.”
Soar to:
Major gains from very low-tech impersonation
From the viewpoint of cybercrime as a business enterprise, the overhead necessary to launch third-party reconnaissance assaults is reduced, according to Hassold it necessitates simple reconnaissance and data collecting, without the need of underlying infrastructure or developers to keep and improve malware. “It’s just sending out e-mails, so from the overhead standpoint it is fantastically valuable,” he mentioned.
3rd-bash impersonation exploits, most of which originate from West Africa, for each Abnormal, use a a few-step procedure (Determine A).
Figure A
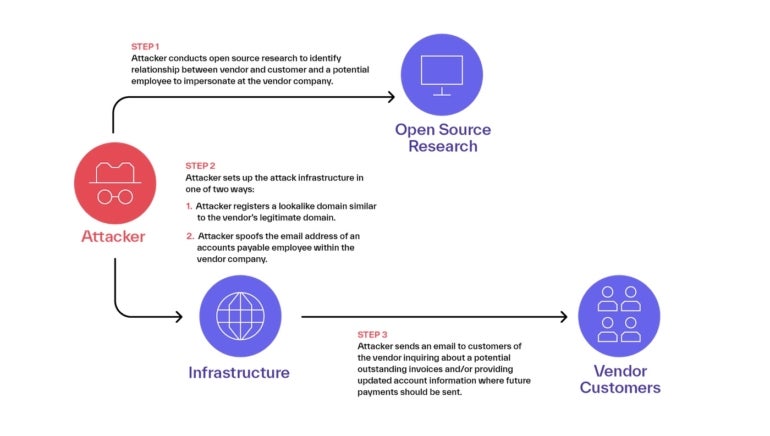
- Open up-supply investigate on vendor consumer relationships, which could occur from condition and community governments that offer you detailed details about present and prior contracts, or a vendor’s web site wherever the company has shown the names or logos of their buyers, or even googling business names to see possible connections.
- Attack infrastructure: The group registers a area, utilizing Namecheap or Google as registrar that impersonates the vendor area, and spoofs the e-mail addresses of accounts payable staff in just the seller firm.
- Qualified electronic mail to prospects: The attacker sends an email to shoppers of the seller inquiring about likely fantastic invoices or offering current account data where long run payments really should be despatched.
Attacking within a week of registering the area title
In accordance to Abnormal Security, Firebrick Ostrich’s use of freshly-registered domains highlights how young domains, in conjunction with other behavioral indicators, can be applied as an successful sign to recognize threats. Abnormal Security reported that 60% of the domains registered by Firebrick Ostrich have been registered on the exact working day as the execution of the BEC marketing campaign in which they are deployed close to 3 quarters of their domains had been acquired inside of 48 several hours of an attack, and 89% of their domains have been registered in a 7 days of a campaign.
SEE: Here’s how IT budgets should fill cybersecurity moats in 2023 (TechRepublic)
Working with the freshly-registered domains, Firebrick Ostrich makes email addresses impersonating actual vendor accounts staff members that they then use to aid their attack, with the primary account communicating with a concentrate on by mimicking a vendor’s precise accounts receivable specialist. The supplemental e mail accounts, which can incorporate financial executives at the vendor, insert a layer of authenticity to their assaults, per the company.
“Reasonable” requests and a extensive-match tactic
Irregular Security’s report explained the preliminary electronic mail in a Firebrick Ostrich attack generally begins with a greeting like the vendor “greatly appreciates you as a valued consumer and we want to thank you for your continued business enterprise,” adopted by two doable requests:
- The very first ask for signifies the vendor would like to update the financial institution account on file with the buyer. The e mail tends to make a level to mention that the seller is not able to acquire payments by way of look at, so ACH and wire transfer payments are the only selections offered.
- The 2nd request inquires about any exceptional payments that are owed to the vendor. The electronic mail states that the seller has shed observe of open up invoices on their conclusion because their accounting staff is not able to evaluation accounts. In 1 email, Firebrick Ostrich provided a lot more information, stating that the account staff is “not capable to get onto the server or into Oracle to evaluation accounts or publish payments that may well have been gained.”
“The produced pretext of a technological problem is a frequent excuse used in several of the 3rd-social gathering reconnaissance attacks we see to describe why a seller isn’t capable to access their individual inventory of invoices, but the flattery demonstrated listed here looks to be special to this BEC group,” explained Hassold.
Yet another tactic is specifically stealthy mainly because it does not request payment for a present-day bill, but merely asks that a vendor’s saved bank account details be current so any long run payments get redirected to the new account. This sidesteps red flags that accounts payable professionals may well have been trained to notice, according to Abnormal Security. The lengthier sport is that the danger actors will get paid with the following bill, as a substitute of the real seller.
What will make this group fairly unique is that they have viewed significant success even without the need of the have to have to compromise accounts or do in-depth exploration on the seller-client romance. By employing reasonably clear social engineering techniques, they can find all the things they need in order to operate a prosperous BEC marketing campaign — without having investing any major time or resources into the first study, for each Abnormal Stability.
The ideal protection is holistic screening
Hassold stated that e-mail-flagging technologies that recognize static indicators won’t be sufficient to protect from BEC assaults he advised a more holistic defense utilizing this sort of strategies as behavioral assessment to understand the romance among the sender and recipients. This holistic tactic would also include info about the target company’s 3rd-get together vendor ecosystem and keep track of the two for precise impersonation attacks spoofing those distributors and suspicious language and artifacts.
“Understanding what tendencies are staying seen in the over-all cyberthreat landscape and generating sure staff are mindful of these are important,” he explained. “That suggests when they see a Firebrick Ostrich-variety assault with requests for an account alter or messages about complex challenges, there is currently an inside policy in spot to validate people requests offline with the seller properly before variations are truly made. We feel of cyberattacks as extremely subtle things, but at the stop of the day a large bulk are nothing at all much more than social engineering, trying to manipulate human conduct — obtaining somebody to do a little something they wouldn’t usually do.”
With cybersecurity assaults very likely to rise this calendar year, and menace actors turning into additional complex in their techniques, this also could possibly be a superior time to place on the white hat. Understand the ropes for $30 with these 9 ethical hacking classes offered via TechRepublic Academy.
[ad_2]
Source backlink New cybersecurity attacks have become increasingly more dangerous and effective. Recently, a particularly dangerous type of attack known as Business Email Compromise (BEC) has been identified.
In a BEC attack, hackers use deceptive emails to impersonate a legitimate vendor in an attempt to make a financial or data transfer. The malicious emails are often complete with legitimate details to deceive the recipient, such as replicated logos and mimic communication styles.
The alarming attack trend is intended to dupe businesses or individuals into making fake payments by pretending to be a trusted vendor. The deception is thorough, with many of the emails sent appearing to be from legitimate suppliers and asking that payment be remitted to a different bank account.
These attacks have already caused losses of millions of dollars to companies in the United States and other countries. The complexity of the attack means that it is hard to protect against it without continuing to educate staff members about how to spot malicious emails.
BEC attacks take advantage of outdated security procedures and lack of training, which is why businesses must be up to date on the latest cybersecurity practices and protocols. There should be strict policies and guidelines regarding approving or processing payments to newly introduced vendors. Also, companies should implement methods to cross-check emails from vendors and verify that their contact details and other information is accurate.
BEC attacks require careful consideration and vigilance by businesses in order to prevent becoming the target of these attacks. Companies must be aware of the threats these attacks present and take appropriate steps to protect their information.