Most Higher Ed Domains Not Protecting Email Security Fully — Campus Technology

Cybersecurity
DMARC Research: Most Better Ed Domains Not Safeguarding Email Protection Totally
New study demonstrates that an mind-boggling majority of education institutions in the United States have incorrectly configured e-mail security options and as a final result are additional prone to phishing and spoofing threats.
The report from email safety provider EasyDMARC reviewed the stability guidelines of .edu email domains, which are assigned to 1,930 U.S. higher schooling establishments. The researchers located that only 152 — or a mere 7.8% — of the country’s .edu domains have correctly applied and configured protection insurance policies to flag, report, and take out outbound phishing emails.
The survey reviewed the deployment of the Area-based Concept Authentication, Reporting and Conformance (DMARC) regular amid .edu domains, first published in 2012. The conventional enables the computerized flagging and removal of receiving e-mail that are impersonating senders’ domains, which EasyDMARC described as “a very important way to avoid outbound phishing and spoofing tries.”
Though 58% of U.S. .edu domains experienced implemented the DMARC conventional, more than 9 in 10 were not totally executed in a method that deploys all of DMARC’s abilities, EasyDMARC explained in its report, “DMARC Tutorial for Education and learning IT Staff.”
Vital Findings of the EDU Domain Analyze
Among the the .edu domains that had implemented DMARC, 848 or 76% ended up applying DMARC only to keep an eye on outgoing e-mail impersonating genuine domains.
-
199 or 18% of DMARC-applying .edu domains ended up only slightly more full in their implementation, getting also set their insurance policies to deliver impersonating email messages to quarantine.
-
152 establishments — 7.8% of all .edu domains, equaling 14% of DMARC-using .edu domains — had DMARC established to routinely reject site e-mails impersonating their domain.
The establishments not using the comprehensive DMARC abilities “leave customers vulnerable to however getting phishing e-mail … and creates a significant possibility for ransomware assaults, fraud, and information breaches,” mentioned the report.
“It’s pretty regarding to see that a lot less than a person in ten U.S. bigger ed institutions have adopted sufficient protection versus (ohishing and spoofing) attacks by sufficiently utilizing a DMARC answer,” stated EasyDMARC CEO Gerasim Hovhannisyan.“With lots of companies going to cloud-centered electronic mail ecosystems, it’s most likely that many instructional institutions are obtaining it tricky to discover a way to apply DMARC that can function seamlessly along with their SaaS solution stack. For sellers and support providers to educational institutions, these findings must be a wake-up get in touch with about the enormous protection gap that wants to be loaded with cloud-indigenous DMARC options.”
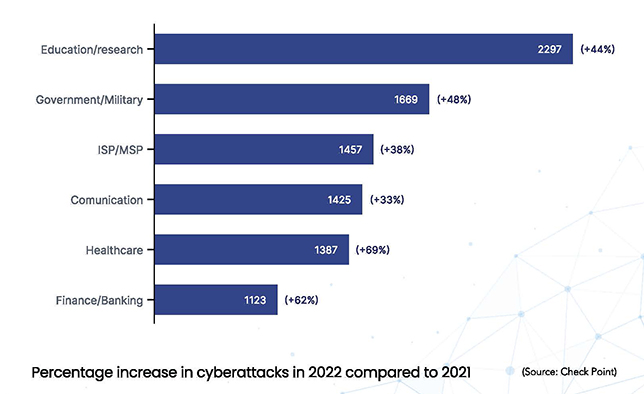
The report observed that in the 1st six months of 2022, the instruction and investigation sector saw a 44% maximize in cyberattacks globally, and in accordance to Checkpoint’s 2022 Cyber Attack Tendencies Mid-12 months Report, schooling was the most specific marketplace for the period.
 The Checkpoint details also displays that electronic mail-delivered assaults comprised 89% of all “in the wild” cyberattacks for the duration of that period of time. Also widely noticed ended up destructive “Microsoft documents” attachments offering malware — symbolizing 61% of all malware attacks.
The Checkpoint details also displays that electronic mail-delivered assaults comprised 89% of all “in the wild” cyberattacks for the duration of that period of time. Also widely noticed ended up destructive “Microsoft documents” attachments offering malware — symbolizing 61% of all malware attacks.
[ad_2]
Source website link It should be noted that most domains associated with higher education are not providing full protection for email security. This finding, according to a recent study conducted by security firm Vade Secure, raises alarms for universities and colleges who rely heavily on email to convey important and often sensitive information.
The research found that while education domains have implemented basic protection such as SPF, DKIM, and DMARC, anti-spoofing and phishing protection is either inadequate or non-existent. For those unaware, these mechanisms are the first line of defense against phishers and malicious actors who use email to infiltrate networks, gather personal information and perpetrate other cybercrimes.
The importance of reliable email security for higher education institutions cannot be underestimated. Many colleges and universities have become increasingly digital and rely on email for student and staff communications, online coursework and other digital deliverables. Thus, comprehensive protection of this channel could save institutions from experiencing a breach and the associated financial and reputational losses.
The findings from the Vade Secure research suggest that many higher education institutions remain woefully unprepared when it comes to defending against email threats. Further increasing the concern is the fact that 96 percent of institutions studied were not using DMARC, a tool that helps detect email spoofing and other malicious activity.
Ultimately, the results of the study cannot be ignored. Education domains must take the necessary steps to ensure their email security strategies are up-to-date and effective. In doing so, they will not only be protecting the personal information of their staff and students, but also safeguarding their institution’s legacy and reputation.