Cloud security, hampered by proliferation of tools, has a “forest for trees” problem

[ad_1]

A new examine Networks identified that, on typical, companies count on more than 30 tools for in general security, and that diploma of complexity is earning for much less security, not a lot more.
About 60% of companies have been running in a cloud ecosystem for a few or a lot more years, but technological complexities and keeping thorough stability nonetheless hamper their cloud migration efforts, according to the 2023 Condition of Cloud-Native Protection Report.
SEE: CrowdStrike: Attackers concentrating on cloud exploits, knowledge theft (TechRepublic)
3 quarters of respondents to Palo Alto Networks’ survey claimed the amount of cloud security applications they use results in blind spots that have an effect on their potential to prioritize danger and avert threats. More than a few quarters claimed they wrestle to recognize what stability tools are important to obtain their goals.
90% of C-Suites respondents reported they could not detect, comprise and take care of cyberthreats within just an hour, and about fifty percent conceded that a the vast majority of their workforce doesn’t understand their stability responsibilities.
Soar to:
Prime problems to furnishing comprehensive security, prime to base, still left to appropriate
Respondents to the Palo Alto Networks’ study named the top rated worries to furnishing detailed safety, which consist of the following:
Running safety holistically throughout teams
It isn’t plenty of to adopt a responsibility model in between cloud service providers and end users firms need to have to seem inward, and reduce silos insofar as they avoid security processes that function for improvement, functions and protection.
Embedding stability throughout the cloud-native improvement lifecycle
Embedding the right cloud protection options at each and every stage of the application development approach from code to runtime is essential.
Teaching IT, enhancement and protection employees to use stability equipment
Cloud-indigenous software enhancement calls for securing “exponentially far more cloud assets across code, workloads, identities, data, etcetera., and across numerous execution environments, this sort of as containers, serverless, and platforms,” pointed out the company.
Lack of visibility into protection vulnerabilities across cloud methods
Palo Alto Networks calls vulnerability administration the “holy grail of application safety.” But attaining this implies staying equipped to mirror the scale, velocity and agility of the cloud, in accordance to the enterprise. Productively completed, it can reward firms with close to genuine-time detection of threats and vulnerabilities.
Using the correct applications
In the report, the excellent cloud protection answer is scalable and equipped to cope with instant stability requires and supplemental use instances as the business expands cloud apps and utilizes.
C-Suites executives not sure about safe cloud deployment
The report is dependent on a survey of 2,500 C-level executives all over the world in November and December 2022 that tracked enterprises’ shift from on-premise software package and services to the cloud and identified a typically weak safety posture. A prevalent concept among the executives surveyed was that their companies require to boost visibility into various clouds as perfectly as incident reaction and investigation.
“With 3 out of four organizations deploying new or updated code to creation weekly, and almost 40% committing new code each day, no 1 can find the money for to forget about the safety of cloud workloads,” said Ankur Shah, senior vice president, Prisma Cloud, Palo Alto Networks.
“As cloud adoption and enlargement carries on, companies have to have to adopt a platform method that secures programs from code to cloud across multicloud environments.”
5 keys to ideal-in-course protection capabilities and ease of use
According to the study, the leading things providers think about when picking out stability alternatives for their cloud purposes had been:
- Ease of use.
- Most effective-in-class capabilities.
- Possible impact on enterprise functionality.
- Familiarity with seller or tool.
- Competitive pricing and/or charge.
The survey uncovered that enterprises are split involving a solitary protection vendor/device approach and a numerous protection vendor/resource tactic for just about every of their safety desires.
Providers keep way too numerous protection arrows in their quivers
3 quarters of the leaders Palo Alto surveyed explained they struggled to determine which protection tools were needed to accomplish their targets, which led to deploying a lot of single place safety methods — of the 30-plus security instruments on typical that corporations are working with, six to 10 are dedicated to cloud safety.
SEE: Open source code for industrial application applications is ubiquitous, but so is the risk (TechRepublic)
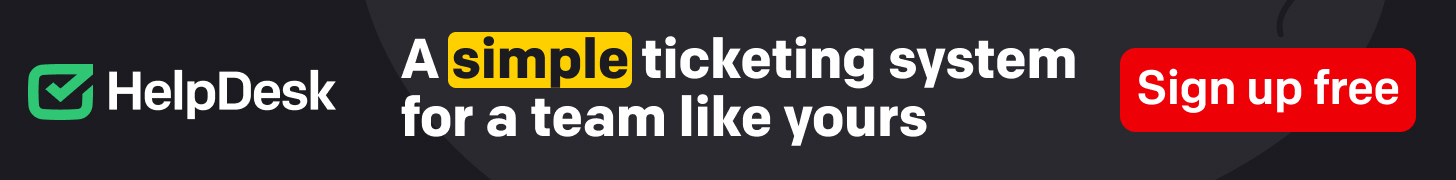
A quarter of respondents described working with equally in-house and open up resource applications, with most of the companies polled indicating they deploy various vendors to secure their clouds, networks and programs (Determine A).
Determine A
Safety gaps persist in spite of efforts
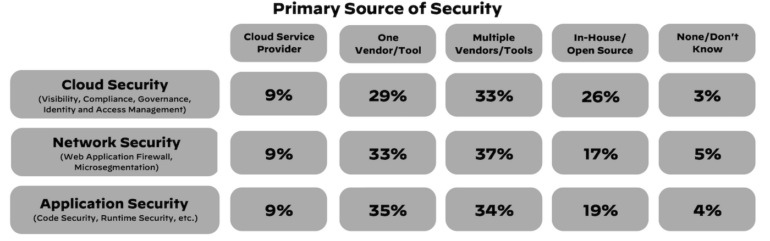
Palo Alto Networks’ analyze described that only about 10% of respondents could not detect, consist of and solve threats in fewer than an hour. In addition, 68% of organizations have been not able to even detect a security incident in much less than an hour, and amongst those that did, 69% could not reply in less than an hour (Determine B).
Determine B
How to stay away from blind places and bad overview of protection risk
Tips from the study’s authors incorporate immediately pinpointing anomalous or suspicious behaviors that show a compromise, and focusing on the signifies of raising around-continuous visibility of cloud property, in component by reducing blind places induced by the absence of a holistic method to safety instrument deployment. The authors also suggested:
Include protection at all stages
Security teams ought to have a in depth knowing of how their firm goes from advancement to generation in the cloud to discover the least disruptive insertion points for protection resources.
“Starting by elevating visibility and resolve-recommendations for program with regarded vulnerabilities and container image scanning is a great initially move towards obtaining early invest in-in from DevOps or system groups,” the report explained.
Undertake risk prevention approaches
Deployment ways can actively block zero-day attacks and contain lateral motion in the party of a breach. Also, work out internet-successful permissions across cloud means to assure greatest practices for minimum-privilege entry.
“At the pretty least, companies should take into consideration applying prevention options to their mission-important programs,” mentioned Palo Alto.
Align cyber tactics with cloud existence
Don’t stop up with dozens of equipment siloed for precise protection use cases in the cloud, top to what Palo Alto Networks phone calls a “sprawl” of equipment that bathroom down cloud stability groups and depart visibility gaps. The corporation indicates reviewing cloud adoption aims about a two to 5 year span.
Consolidate equipment where by achievable
Unify info and stability controls into a system method to attain a complete perspective of danger, compared to the granular sights presented by many siloed instruments.
“By consolidating tools, protection teams can automate correlation and deal with the most vital safety challenges throughout the application lifecycle,” mentioned the firm.
Acting quickly when an incident occurs depends on a robust plan
Protection incidents on desktops and other gadgets, networks, purposes and cloud products and services platforms necessitates a rapid response. The sooner just one reports to IT and relevant safety teams the greater when receiving suspicious messages, noticing strange alterations to program or product performance, discovering a misdirecting connection or any other suspected attack or infiltration. Obtain TechRepublic Premium’s Stability Incident Reaction Coverage to study finest techniques for incident reaction.
[ad_2]
Resource connection For many organizations, cloud security has become a top priority in recent years as they shift their data and applications to the cloud. However, many organizations find themselves struggling to effectively secure their cloud environment due to the proliferation of cloud-based tools, platforms, and services. This challenging landscape can make it difficult to identify weak links and vulnerabilities, leading to a “forest for the trees” problem.
The addition of multiple cloud services has significantly complicated the security landscape, as organizations must take into account the myriad of connections, controls, and policies that must be managed across each service. The trend of using multiple tools and services can further increase complexity. The result is that many organizations are unable to effectively manage their cloud security, leading to potential security gaps and vulnerabilities going unnoticed.
Organizations must take a comprehensive and integrated approach to cloud security in order to effectively tackle the “forest for trees” issue. This begins with the adoption of a well-defined cloud security strategy that outlines the process for identifying, monitoring, and responding to potential security threats. This can include cloud security tools and services that can help organizations detect any potential vulnerabilities. Organizations should also employ a combination of automated security scans, manual assessments, and access controls to prevent the creation of security gaps.
Organizations must also remain vigilant and regularly audit their cloud environment to ensure security policies are being properly enforced. Establishing a comprehensive cloud security process is essential in order to mitigate any potential risks associated with the proliferation of cloud-based tools, platforms, and services.
Ultimately, cloud security must not be overlooked in an organization’s overall security strategy. It requires a proactive approach to security that looks beyond the individual layers of the cloud to identify potential gaps and vulnerabilities. By taking a comprehensive, integrated approach to cloud security, organizations can better secure their cloud environments and avoid the “forest for trees” problem.